Chmod in Recursive: How to Change Permissions in Linux?

Introduction
In the vast realm of Linux system administration, the chmod command stands as a stalwart guardian, allowing users to modify file and directory permissions with precision. However, when it comes to managing permissions at scale, the need for a recursive approach becomes paramount. In this guide, we delve into the intricacies of Linux chmod recursive command, unraveling the steps to efficiently change permissions across directories and their subcontents.
Check File Permission

In the intricate tapestry of Linux system administration, understanding and verifying file permissions are quintessential tasks. This section will guide you through the process of checking file permissions with a specific focus on the recursive capabilities of the chmod recursive command.
Before we embark on the journey of Linux chmod recursive mastery, let’s briefly grasp the concept. Recursive, in the context of permissions, implies the extension of modifications to encompass all nested directories and files within a specified directory. This proves invaluable when you need to apply uniform permissions throughout an entire directory tree.
Verifying Permissions for a Single File:
Before diving into recursive checks, let’s begin with the basics. To inspect the permissions of a single file, the ls command in conjunction with the -l flag is your trusted ally. For instance:
ls -l filename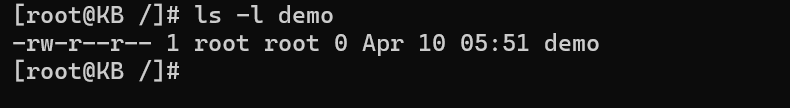
This command yields a detailed listing, presenting ownership details, permissions, and more.
The output might resemble:
-rw-r--r-- 1 user group 1024 Dec 13 12:00 filenameBreaking down the permissions section (rw-r–r–), we observe the owner has read and write permissions, while the group and others have only read permissions.
Recursive Permission Checks on Directories:
Now, let’s elevate our perspective to encompass entire directory structures. The ‘-R’ flag with the ls command allows recursive exploration:
ls -lR /path/to/directory 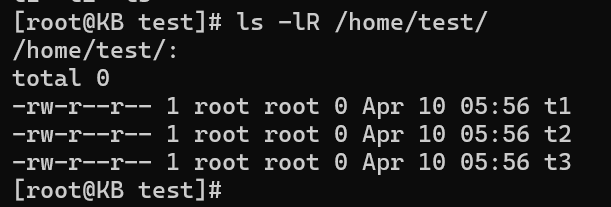
This command drills down into the specified directory and its subdirectories, providing a comprehensive overview of permissions for all contained files and directories.
Leveraging Linux chmod Recursive command to Inspect and Modify:
To check permissions and potentially modify them recursively, the Linux chmod recursive command continues to be our protagonist. Consider the following example:
chmod -R 755 /path/to/directory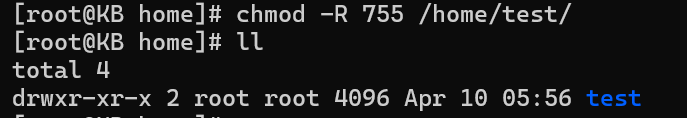
In this instance, the ‘-R’ flag ensures that the permissions change applies not only to the specified directory but permeates through its entire hierarchy. The ‘755’ mode grants the owner full permissions and read/execute permissions to group members and others.
Ensuring Security with chmod 777 Example:
While powerful, the ‘chmod 777’ command should be approached with caution, as it grants unrestricted read, write, and execute permissions to all users. Only employ this when absolute openness is necessary, and security implications are thoroughly considered:
chmod -R 777 /path/to/directory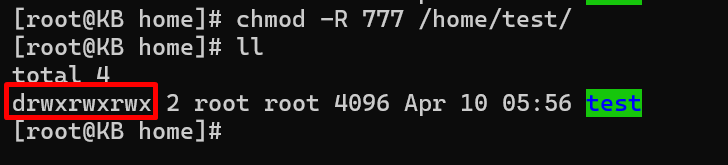
Change Permission Recursively

In the dynamic landscape of Linux administration, the ability to modify permissions at scale is an indispensable skill. This section delves into the intricacies of changing permissions recursively using the Linux chmod command, shedding light on effective techniques and best practices.
The Essence of Recursive Permissions:
Before we embark on the journey of recursive permission changes, let’s grasp the concept. Recursive permissions, in the context of chmod, involve applying modifications not only to a specified directory but to all its nested directories and files. This proves invaluable when a uniform access control policy needs to be enforced across an entire directory tree.
The Recursive Power of chmod:
The chmod command, a linchpin in permission management, becomes even more potent when coupled with the ‘-R’ flag. This flag signals the command to operate recursively, extending the modifications throughout the directory hierarchy. Let’s illustrate the process with a practical example:
chmod -R 755 /path/to/directory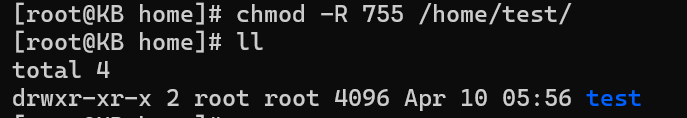
In this command, the ‘-R’ flag ensures that the permission changes cascade down from the specified directory to every file and subdirectory within its structure. The ‘755’ signifies the permission mode, granting read, write, and execute permissions to the directory owner, and read and execute permissions to group members and others.
Practical Use Cases:
Empowering Full Access:
There are scenarios where you might need to grant full permissions to a directory and its contents. The following command achieves this with the ‘chmod 777’ mode:
chmod -R 777 /path/to/directory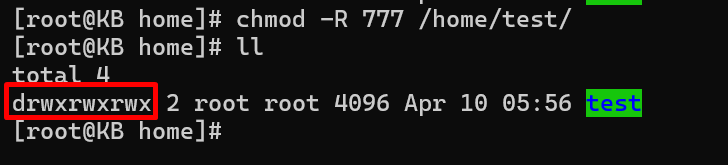
Caution is warranted when using 777 permissions, as it provides unrestricted access to all users.
Striking a Balance for Security:
Security-conscious administrators often opt for a more measured approach. The following example sets read and execute permissions for the directory owner, read permissions for the group, and read-only permissions for others:
chmod -R 744 /path/to/directory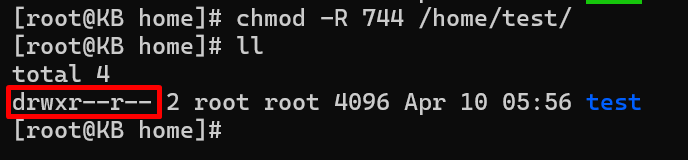
Considerations for Responsible Permissions Management:
Evaluate Security Implications:
Before applying recursive changes, carefully assess the security implications of the chosen permission mode, especially when contemplating 777 permissions.
Backup Critical Data:
Before executing recursive permission changes, consider backing up critical data. This precaution ensures that unintended consequences can be rectified without loss.
Change Permission With the find Command

Precision and efficiency are paramount when it comes to managing file and directory permissions. This section explores an advanced technique for changing permissions recursively using the find command in conjunction with chmod, offering a nuanced approach to access control.
The Synergy of find and chmod:
The find command, renowned for its versatility in locating files and directories based on various criteria, seamlessly integrates with chmod to provide a robust solution for recursive permission changes. This method allows administrators to target specific files or directories within a hierarchy, offering more surgical precision compared to traditional recursive changes.
Syntax and Application:
The basic syntax for changing permissions with find and chmod is as follows:
find /path/to/directory -type f -exec chmod 644 {} \;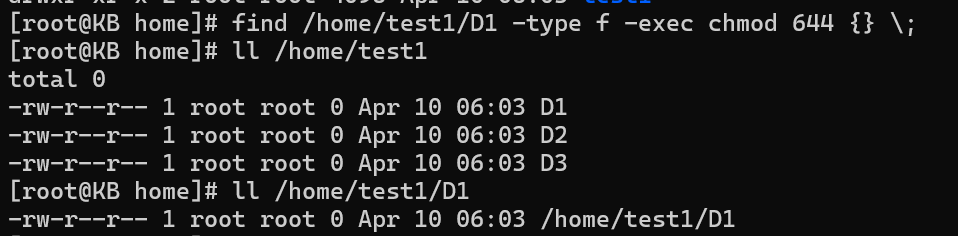
find /path/to/directory -type d -exec chmod 755 {} \;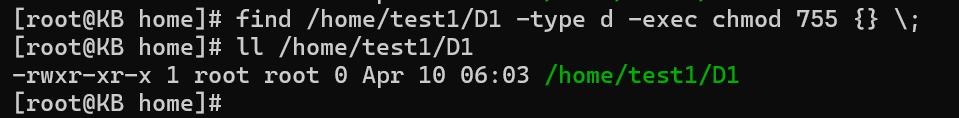
Breaking down the command:
The first line modifies permissions for files (-type f) within the specified directory, setting read and write permissions for the owner and read-only permissions for group members and others (chmod 644).
The second line targets directories (-type d), providing read, write, and execute permissions for the owner and read/execute permissions for group members and others (chmod 755).
This approach ensures a granular adjustment of permissions tailored to the nature of the file or directory.
Practical Example:
Let’s consider a scenario where you want to grant read and execute permissions to all directories and their contents within a specific path:
find /path/to/directory -type d -exec chmod 711 {} \;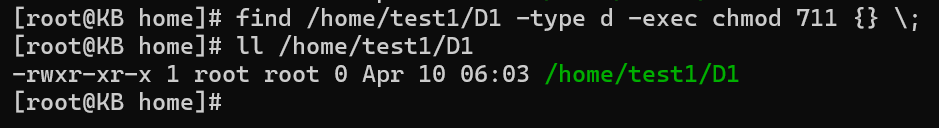
find /path/to/directory -type f -exec chmod 644 {} \;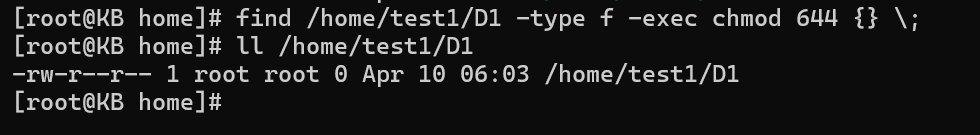
In this example, the command differentiates between directories and files, applying distinct permission sets.
Advantages of the Find Approach:
Selective Permissions:
The ability to specify permissions based on file type allows for a more nuanced control strategy. For instance, ensuring executable files have restrictive permissions while granting more open access to non-executable files.
Targeted Changes:
Unlike traditional recursive changes, the find command enables administrators to selectively apply modifications to files and directories that meet specific criteria.
Best Practices:
Test in a Safe Environment:
Before implementing changes in a production environment, test the find and chmod commands on a smaller scale to ensure the desired results.
Understand find Filters:
Familiarize yourself with the various filters and criteria that find support to tailor your commands precisely.
Also Read: How to Use the xargs Command in Linux?
Change Permission of Specific Files Recursively

Under the Linux system administration, there are instances where a targeted approach to permission changes becomes imperative. This section sheds light on how to wield the power of chmod in recursive mode to selectively modify the permissions of specific files within a directory hierarchy.
The Need for Precision:
While recursive permission changes are robust, situations arise where only specific files require tailored access controls. This could be due to security considerations, application requirements, or other nuanced scenarios. Enter the granular control offered by chmod in tandem with careful file selection.
Crafting the Command:
The fundamental structure of the command involves leveraging find to identify specific files and then applying chmod for permission modifications. Consider the following example, where we aim to grant read and write permissions to all .txt files within a directory and its subdirectories:
find /path/to/directory -type f -name '*.txt' -exec chmod 664 {} \;Breaking down the command:
find /path/to/directory: Specifies the target directory.
-type f: Filters for files only, excluding directories from the search.
-name ‘*.txt’: Narrows down the search to files with the .txt extension.
-exec chmod 664 {} \;: Executes chmod 664 on each found file, granting read and write permissions to the owner and group, and read permissions to others.
Practical Example:
Let’s say you want to restrict access to all files with the extension .conf within a directory and its subdirectories:
find /path/to/directory -type f -name '*.conf' -exec chmod 600 {} \;In this case, the command ensures that only the file owner has read and write permissions, enhancing the security of configuration files.
Advantages of Targeted Changes:
Security Compliance:
Tailoring permissions to specific file types ensures that sensitive or configuration files adhere to security best practices.
Customized Access:
Application-specific files can receive permissions that align with their usage, providing a customized access control strategy.
Best Practices:
Backup Critical Data:
Before initiating recursive permission changes, especially when targeting specific files, consider backing up critical data to mitigate the risk of unintended consequences.
Test in a Controlled Environment:
Conduct tests in a controlled environment to validate the accuracy and effectiveness of your find and chmod commands before applying changes in a production setting.
Also Read: 50+ Linux Commands with Screenshots
Conclusion
Our exploration of chmod in recursive mode unveils a profound understanding of access control intricacies. Navigating this terrain requires mastery of the versatile Linux chmod recursive command, which, with the addition of the -R flag, transforms into a potent tool for uniform permission changes across entire directory hierarchies. Furthermore, the integration of found elevates precision, enabling administrators to selectively modify permissions for specific files. From the broad strokes of chmod 777 example for comprehensive access to nuanced commands tailored with find, our journey encompasses diverse scenarios, emphasizing the importance of balancing openness with security.
As we conclude, the emphasis on responsible administration resonates. The best practices outlined, such as prioritizing security considerations, conducting thorough testing, and leveraging the precision of findings, underscore the importance of deliberate and informed decision-making in permission management. This holistic approach empowers Linux administrators to sculpt access controls that align with the unique needs of their systems, ensuring a secure, controlled, and seamless journey through the intricacies of file and directory permissions in the Linux environment.




